Prioritise cybersecurity in 2022

The ransomware attack on the HSE’s IT system in May 2021 showed Ireland that cybersecurity can no longer be taken for granted, writes David Curtin, CEO of .IE, the company that manages .ie, the preferred online address for business in Ireland.
Most importantly, it alerted the Irish Government to the dangers of an under-resourced cyberdefence network. Since the attack, it has pledged €2.5 million in funding for the National Cyber Security Centre. This is good news; more resources will help protect Ireland’s critical infrastructure from future disruption.
The EU, too, is funnelling more money and minds towards cybersecurity threats. The Commission presented its plan for the Joint Cyber Unit in June; if approved, it will allow member state capitals to pool resources and provide mutual assistance should a catastrophic cyberattack occur.
Two new EU laws, updates to NIS2 (Security of Network and Information Systems Directive) and CERD (Critical Entities Resilience Directive), will require critical sectors to have more robust cybersecurity policies, reporting procedures, and stronger physical protection of their technical infrastructure.
This increased cybersecurity awareness is not a coincidence. There has been a dramatic increase in our usage, reliance and dependence on digital tools, systems and applications during a year and a half of lockdowns and semi-restricted trading. A successful cyberattack could conceivably put many SMEs out of business. Indeed, according to a 2021 Hiscox report, one in six businesses surveyed said a cyberattack this year had ‘materially threatened the solvency or viability of the company’. The same Hiscox report shows that the median cost of an attack on a micro-business is $8,000. SMEs, which make up 99 per cent of Irish businesses, are regular targets for cybercriminals.
From .IE’s work with SMEs, including our .IE Digital Town programme1 and
.IE Tipping Point research2, we know that when it comes to digital, SMEs are frequently concerned about a lack of skills, time, and money. This means many SMEs de-prioritise important digital best practices, such as cybersecurity. Fortunately, the risk of being a victim of a cyberattack can be decreased dramatically with good security hygiene.
United we stand
The beginning of a trend towards greater cooperation between government bodies, business and law enforcement is a very welcome development in the fight to contain damage inflicted by cyber criminals. Clearly, we are stronger if we are united in building defences and cyber skills.
Guided by its multi-stakeholder policy advisory committee, .IE has commissioned a third party to provide ongoing monitoring and alerting services for its registrar/hosting channel. To date the service has helped over 300 SMEs and citizens, who are innocent victims of attacks related to phishing, bots and malware which had targeted their .ie domains.
In addition, .IE has protocols with regulatory bodies, see www.weare.ie/governance for more detail, which result in suspension or deletion of .ie domains which operate fake webshops or offer for sale banned products, services or medicines.
Thanks to the managed registry model operated by .IE, Ireland has a less risky namespace when compared to .com or .co.uk. All new .ie domain registrations require documentary proof of a connection to Ireland, which is then manually verified by the .IE team.
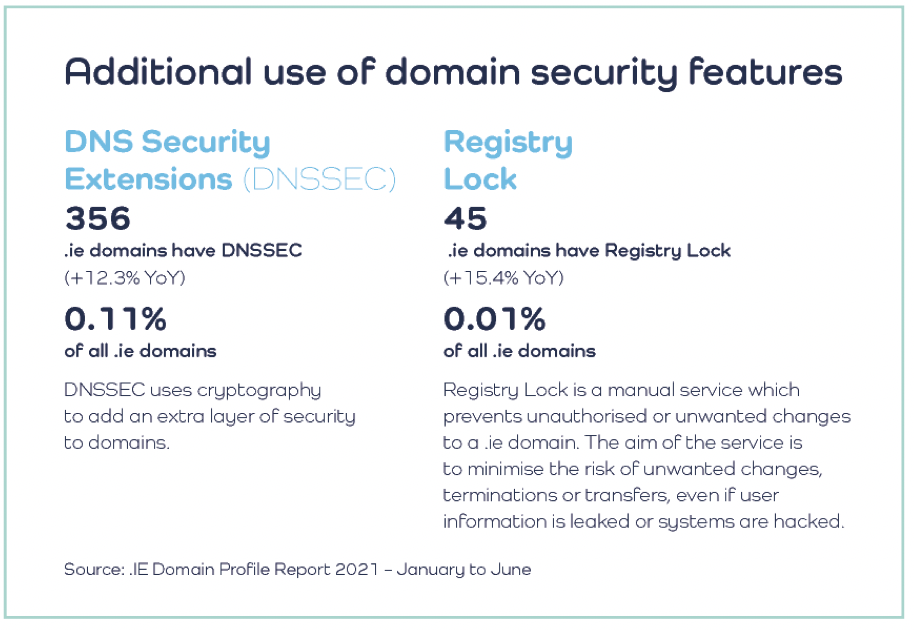
Owners of .ie domains can also avail of two additional security features that are provided by the registry: DNSSEC and Registry Lock. DNSSEC uses cryptography to add an extra layer of security to users’ networks, while Registry Lock protects a domain from malicious or accidental modification.
All .ie website owners can also avail of an independently provided security certificate, which proves to visitors that a website is legitimate and secure. Our analysis shows that 40 per cent of .ie websites have security certificates. While it isn’t yet a majority, it demonstrates that the number of active .ie websites had a 44 per cent increase year-on-year.
Recognising cyber scams
Most attempts at malicious entry to a computer network are opportunistic. Billions of personal and commercial email addresses and phone numbers are in circulation on the dark web. Hackers will routinely target large segments of these addresses and numbers in the hope that a tiny percentage of people will fall for their scam.
As a result, the vast majority of successful cyberattacks depend entirely on deception. For example, a hacker might send an email that appears to be from a legitimate company, such as a bank, courier, or a subscription service that someone is likely to use, such as Netflix or Amazon. Typically, these emails claim that the user’s account will be deleted if they do not take action. The user is directed to a dummy login page and enters their password and payment details, which are then stolen. This form of attack is described as a phishing attack.
Other malicious emails request that you download a file, which is typically an executable file (.exe) disguised as an image, text document, or spreadsheet. When the user opens and initialises the file, the ransomware is deployed. The effect may be immediate or take days, weeks, or even months to surface, but the consequences are always the same: the user is logged out of its systems, when the hard drive is maliciously encrypted by the hacker. An automated message demands payment for the decryption key.
Security hygiene
All organisations, including SMEs, can take some basic steps to drastically reduce the likelihood of a cyberattack occurring:
1. Take updates seriously
It’s easy to dismiss your antivirus or operating systems update notifications during a busy workday, but it’s in your organisation’s best interests to act quickly and install them.
These updates typically fix security holes in software, which hackers are notoriously quick to spot and exploit. Ensure all employees update when prompted. Security experts strongly recommend that you automate this task, to make it mandatory, and less prone to human lapses in security discipline.
2. Enforce your passwords policy
With more services and suppliers requiring sign-up details comes the temptation to reuse old passwords. While it’s convenient in the moment, the downside is that if your password becomes known to a hacker, all your accounts are at risk.
By using a password manager, such as 1Password or Dashlane, you only need to remember one master password. The password manager will create random passwords for all your other accounts, securing them with encryption.
3. Be on your guard
If an email offer seems too good to be true, it probably is. Sceptically interrogating suspicious messages can be the difference between business as usual and a costly mistake.
Never open an attachment from a suspicious email’s sender. If in doubt, employees can check an address by safely hovering over it or clicking ‘more details’ in their email client. Be on the lookout for inconsistencies, unusual email addresses and mis-spelled domains.
4. Protect laptops when working from home
Using company laptops when working from home became commonplace during the Covid lockdown. Employees should be instructed to never, ever let their children or visitors use the company laptop to check their email, play music or surf the web. In particular, never use a personal USB stick device on the company laptop.
Fundamentally, the same cybersecurity principle that applies to multinational corporations and governments applies to micro and small businesses: prevention.
Use a domain from a managed registry, such as .ie. Protect it with further security features, such as DNSSEC and Registry Lock. Acquire a security certificate from a third-party authenticator. Recognise danger and practise good security hygiene, and always update your software when prompted.
Through simple proactive steps, SMEs can drastically reduce their chance of falling victim to an expensive and potentially ruinous cyberattack. Make cybersecurity your organisation’s priority in 2022.
E: marketing@weare.ie
W: www.weare.ie
- www.weare.ie/about-ie-digital-town
- www.weare.ie/tipping-point






